Scam Sniffer Reports: Two Crypto Users Lose More Than $62M to Address Poisoning Scheme
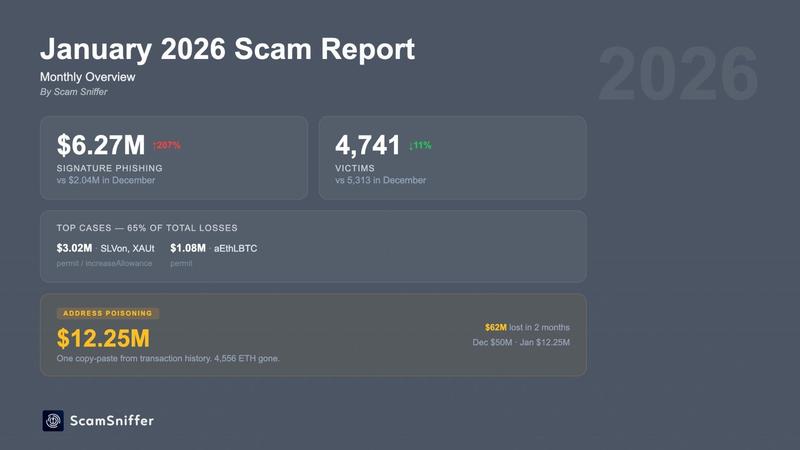
Two cryptocurrency holders have lost a combined $62 million to address poisoning scams since December. January witnessed a dramatic 207% spike in signature phishing incidents as Ethereum dust attacks continue to intensify.

A single crypto holder fell victim to an "address poisoning attack" in January, losing $12.2 million after inadvertently copying an incorrect address from their transaction records, following a comparable $50 million incident that occurred in December, as reported by Scam Sniffer.
The address poisoning technique involves malicious actors dispatching minimal transactions, often referred to as "dust," from wallet addresses that closely resemble legitimate ones found in a victim's transaction history, with the expectation that targets will mistakenly copy the fraudulent address.
According to Scam Sniffer's findings, signature phishing attacks have also experienced a notable uptick in recent weeks, with losses totaling $6.27 million affecting 4,741 individuals throughout January, representing a 207% jump when compared to the previous month of December.
A pair of cryptocurrency wallets were responsible for approximately 65% of the total losses attributed to signature phishing schemes.
The signature phishing method differs somewhat from address poisoning, as it manipulates users into authorizing harmful blockchain transactions, including granting unlimited approval for token transfers.
Address poisoning trend not slowing down
"Address poisoning is one of the most consistent ways large amounts of crypto get lost," security company Web3 Antivirus noted in a report published on Thursday.
The largest address poisoning incidents the firm has monitored over an extended period have resulted in losses spanning from $4 million up to $126 million. "Recent incidents show this trend isn't slowing down," they stated.
According to the research team's explanation, those conducting address poisoning attacks "generate full addresses that match the same first/last few characters you see, but the middle is different, so it looks 'identical.'"
Dust attacks on Ethereum have surged
Industry analysts believe that the Ethereum Fusaka upgrade implemented in December has played a role in the rising number of attacks by reducing transaction costs across the network, making it more economical for attackers to operate.
Dust activity associated with stablecoins is currently estimated to represent 11% of the total Ethereum transactions and encompasses 26% of active wallet addresses on a typical day, as documented by Coin Metrics in their early February report.
The research organization examined more than 227 million balance changes for stablecoin wallets operating on the Ethereum network spanning from November 2025 to January 2026, discovering that 38% of these updates were valued at less than one cent — "consistent with millions of wallets receiving tiny poisoning deposits," it stated.
Whitestream, a blockchain intelligence company, disclosed on Sunday that the decentralized stablecoin DAI "has gained a reputation as a preferred stablecoin for illicit actors, serving as a 'parking place' for illegally sourced funds."
"This is due to the protocol's governance, which does not cooperate with authorities in freezing DAI wallets," it stated, making reference to the recent wave of address poisoning attacks.