SlowMist Discovers Hundreds of Malicious Plugins Infiltrating OpenClaw AI Platform
Cybersecurity firm SlowMist has identified 472 compromised AI skills loaded with harmful code, highlighting how AI plugin marketplaces have emerged as prime targets for cybercriminals targeting cryptocurrency users' systems.
OpenClaw's official marketplace for plugins, an open-source artificial intelligence agent initiative, has fallen victim to supply chain poisoning campaigns, a new analysis from security research company SlowMist reveals.
According to a Monday report from SlowMist, threat actors have been systematically uploading compromised "skills" to ClawHub, OpenClaw's plugin distribution platform, taking advantage of what the firm characterized as inadequate or absent vetting processes. This approach enables malicious code to propagate to unsuspecting users who download and install these plugins, often without awareness of the security implications.
The company stated that MistEye, its Web3-oriented threat detection platform, generated high-severity warnings for 472 compromised skills available on the marketplace.
A supply chain poisoning attack occurs when cybercriminals compromise a software provider or component to embed malicious code before distribution to the final user.
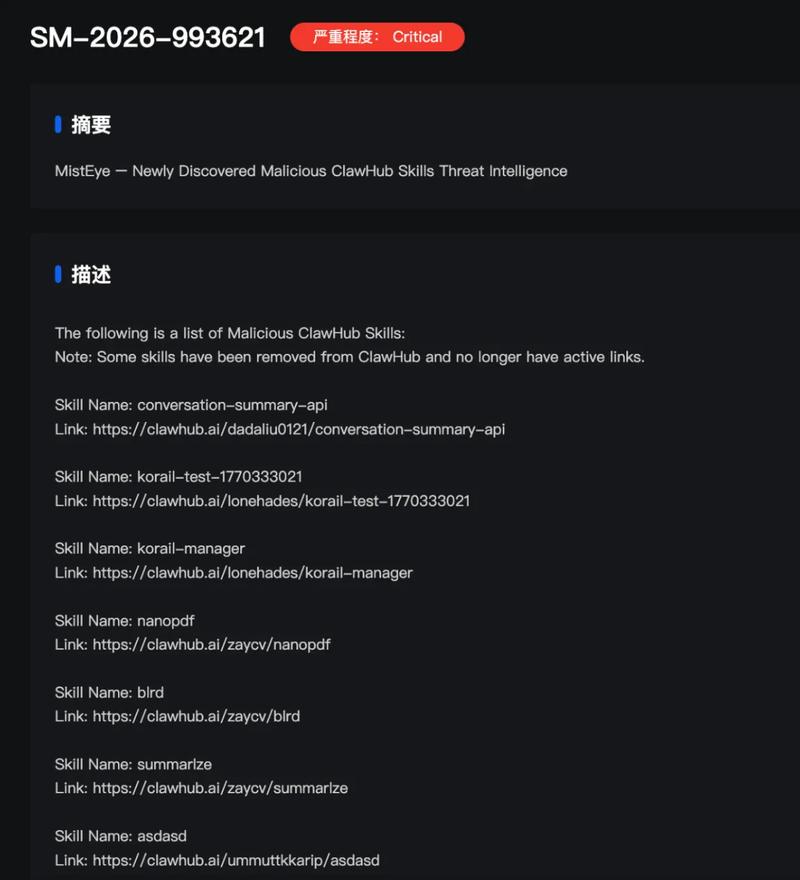
Malicious skills hide backdoors
SlowMist's analysis reveals that the compromised skills disguise themselves as legitimate dependency installation packages, concealing malicious commands that activate backdoor capabilities once downloaded and run, employing a strategy the firm likened to a Trojan horse approach.
After successful installation, the threat actors generally engage in "extortion following data theft," SlowMist reported, since the "Base64" backdoor is capable of harvesting passwords and private files from compromised systems.
The majority of these attacks originate from an identical malicious domain address (socifiapp[.]com), which was registered in July 2025, and the same IP address connected to Poseidon infrastructure exploits.
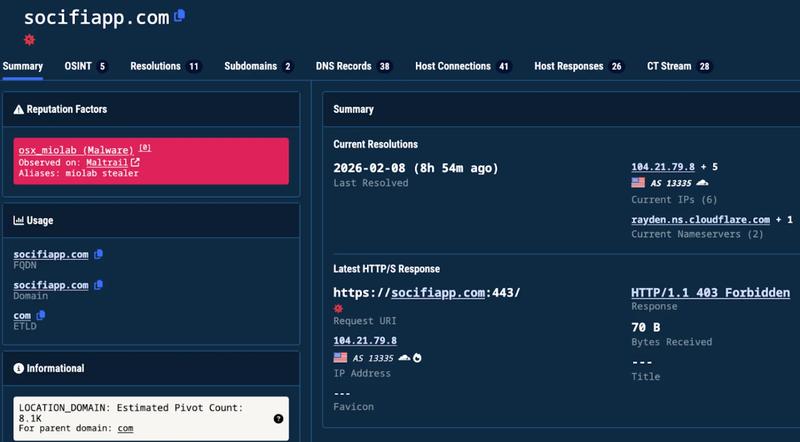
The compromised skills were often labeled using terminology related to crypto assets, financial data and automation tools. SlowMist explained that these are categories designed to reduce users' vigilance and promote rapid installation.
The research findings from SlowMist indicate a larger coordinated campaign by an organized group, given that numerous infected skills reference identical domains and IP addresses.
"This strongly suggests a group-based, large-scale attack operation, in which a large number of malicious skills share the same set of domains/IPs and employ largely identical attack techniques."
Cointelegraph has contacted SlowMist for additional details on which crypto-related AI skills were most heavily targeted.
In a Feb. 1 report, cybersecurity firm Koi Security also flagged that 341 out of the 2,857 analyzed AI skills contained malicious code, reflecting a typical pattern of supply chain poisoning attacks through plugins and extensions.
To avoid falling victim to this threat, SlowMist recommends that users first audit any SKILL.md sources that require installation or copy and paste execution. Users should also be suspicious of prompts that require system passwords, accessibility permissions or ask to execute system configuration changes.